Cyber Security Delinea

ThycoticCentrify is Now Delinea!Delinea was formed in April 2021 through the merger of established PAM leaders Thycotic and Centrify.
Thycotic protects companies from cyber-attacks
by developing innovative technologies that secure privileged accounts across the modern enterprise.
by developing innovative technologies that secure privileged accounts across the modern enterprise.
PROACTIVE, PRAGMATIC SOLUTIONS
TO MEET YOUR SECURITY OBJECTIVES
TO MEET YOUR SECURITY OBJECTIVES
PRIVILEGED ACCESS
MANAGEMENT
MANAGEMENT

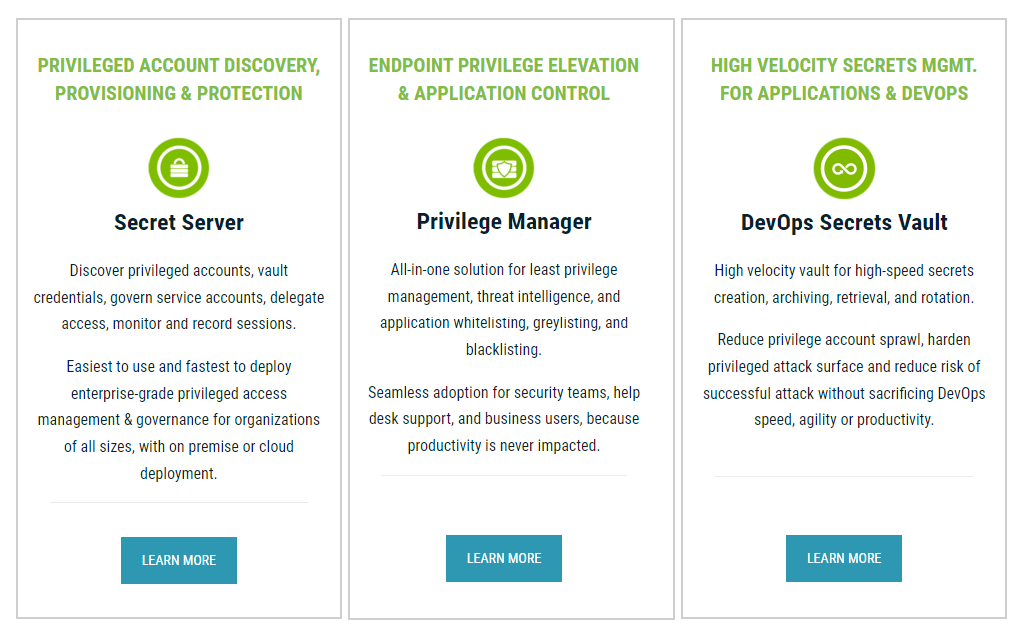
Secret Server
easiest to use, most powerful, and widely adopted privileged access management (PAM) solution.
Enterprise-grade password security and privileged account management for organizations of all sizes and any type of deployment.
LEAST PRIVILEGE &
APPLICATION CONTROL
APPLICATION CONTROL

Privilege Manager
All-in-one solution for least privilege management, threat intelligence, and application whitelisting, greylisting, and blacklisting.
Seamless adoption for security teams, help desk support, and business users, because productivity is never impacted.
PRIVILEGED ACCOUNT
INCIDENT RESPONSE
INCIDENT RESPONSE

Privilege Behavior Analytics
Advanced analytics and machine learning that integrates with your privileged access management solution. Automatically identify and analyze suspicious behavior that indicates privileged account abuse.
Maintain business continuity with real-time alerts that support rapid, effective incident response to a privileged account breach.
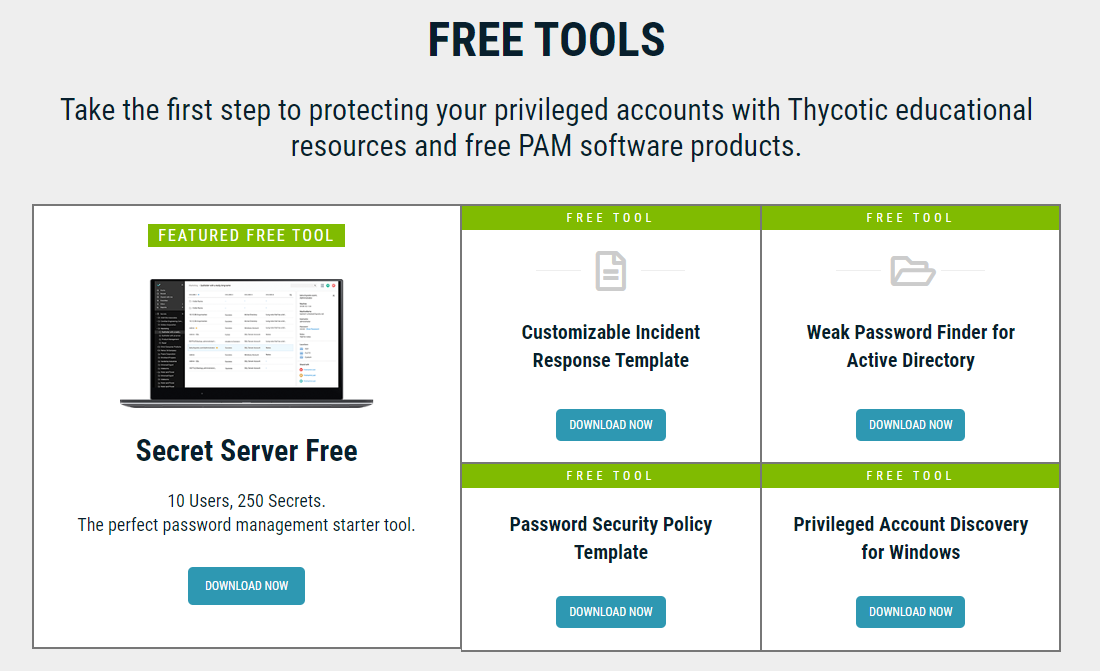
FREE TOOLS
Take the first step to protecting your privileged accounts with Thycotic educational resources and free PAM software products.
FEATURED FREE TOOL
Secret Server Free
10 Users, 250 Secrets.
The perfect password management starter tool.
The perfect password management starter tool.
FREE TOOL
Customizable Incident Response Template
FREE TOOL
Weak Password Finder for Active Directory
FREE TOOL
Password Security Policy Template
FREE TOOL
Privileged Account Discovery for Windows
Audit and Compliance
UNKNOWN, UNMANAGED, AND UNPROTECTED PRIVILEGED ACCOUNTS VIOLATE COMPLIANCE MANDATES
To pass your next compliance audit you must demonstrate effective privilege management.
EVERY MAJOR SECURITY FRAMEWORK AND REGULATION DEMANDS PROPER PASSWORD PROTECTION.
SEE HOW YOUR SECURITY PRACTICES MAP TO COMPLIANCE REQUIREMENTS
Which compliance regulations do you need to follow? How can you satisfy auditors? Some regulations are highly prescriptive while others give you broad guidelines but leave the detailed decisions up to you. See how your privilege management practices stack up to the latest compliance requirements. Make sure you know the deadlines so you can be ready when the auditors arrive.
EU GDPR
Any organization dealing with EU citizens’ Personally Identifiable Information is obligated to meet standards for effective data protection, adequate security measures, and privacy by design to comply with EU GDPR.
Any organization dealing with EU citizens’ Personally Identifiable Information is obligated to meet standards for effective data protection, adequate security measures, and privacy by design to comply with EU GDPR.
NERC/CIP
Under the North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) plan, energy and utility companies must ensure strict access control in order to protect assets from the threat of a cyber attack.
Under the North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) plan, energy and utility companies must ensure strict access control in order to protect assets from the threat of a cyber attack.
CIS Controls
The Center for Internet Security (CIS) Top 20 Critical Security Controls (previously known as the SANS Top 20 Critical Security Controls) is a set of security best practices designed to prevent the most common and significant cyber threats, including password protection.
The Center for Internet Security (CIS) Top 20 Critical Security Controls (previously known as the SANS Top 20 Critical Security Controls) is a set of security best practices designed to prevent the most common and significant cyber threats, including password protection.
NYCRR
One of the strictest cyber security regulations at a federal or state level, NYCRR applies to New York insurance companies, banks, and other regulated financial services institutions, including agencies and branches of non-US banks licensed in the state of New York.
One of the strictest cyber security regulations at a federal or state level, NYCRR applies to New York insurance companies, banks, and other regulated financial services institutions, including agencies and branches of non-US banks licensed in the state of New York.
HIPAA
Any organization that creates, receives, maintains, or transmits electronic protected health information (ePHI) in the US must meet HIPAA requirements for access control and data sharing.
Any organization that creates, receives, maintains, or transmits electronic protected health information (ePHI) in the US must meet HIPAA requirements for access control and data sharing.
SOX
Sarbanes-Oxley (SOX) is designed to reduce corporate fraud by requiring an increase in the strength and granularity of security controls for financial auditing and reporting.
Sarbanes-Oxley (SOX) is designed to reduce corporate fraud by requiring an increase in the strength and granularity of security controls for financial auditing and reporting.
PCI DSS
PCI DSS provides organizations that accept, store or transmit credit card data with guidelines for privilege management and a framework to protect cardholder data.
PCI DSS provides organizations that accept, store or transmit credit card data with guidelines for privilege management and a framework to protect cardholder data.
UK Cyber Essentials
Contractors in the UK that handle sensitive or personal information must receive Cyber Essentials Certification to demonstrate understanding and enforcement of privilege management.
Contractors in the UK that handle sensitive or personal information must receive Cyber Essentials Certification to demonstrate understanding and enforcement of privilege management.
FISMA/NIST
The National Institute of Standards and Technology (NIST) outlines steps federal agencies and government contractors must take to comply with privilege management in FISMA in NIST SP 800-53.
The National Institute of Standards and Technology (NIST) outlines steps federal agencies and government contractors must take to comply with privilege management in FISMA in NIST SP 800-53.
UAE NESA
The National Electronic Security Authority (NESA) in the United Arab Emirates requires government entities and businesses in critical sectors closely control and protect privileged accounts.
The National Electronic Security Authority (NESA) in the United Arab Emirates requires government entities and businesses in critical sectors closely control and protect privileged accounts.
NEW ZEALAND CYBER SECURITY STRATEGY
The refreshed New Zealand Cyber Security Strategy comes with an Action Plan and a National Plan to address cybercrime, which is added to the original four key principles. It replaces the New Zealand Cyber Security Strategy from 2011.
The refreshed New Zealand Cyber Security Strategy comes with an Action Plan and a National Plan to address cybercrime, which is added to the original four key principles. It replaces the New Zealand Cyber Security Strategy from 2011.




 Cyber Security
Cyber Security Infrastructure
Infrastructure Networking
Networking Data Management
Data Management Work Productivity
Work Productivity Video Conference
Video Conference


